Use CryptoLocker to train your incident response team
An incident response and incident investigation team needs to be able to quickly extract useful information from an incident. Instead of writing long theoretical documents I wanted to use the hands-on approach to serve as an example to train a team to quickly extract IOCs from an ongoing incident. What’s better for doing this than to analyze the behavior of CryptoLocker to train an incident response team and analyze the delivery of CryptoLocker?
IOCs or Indicators of Compromise is a set of data that allows your abuse team to defend against computer intrusions.
The information found through this analysis is not new. It’s mostly meant as a demonstration of a thought process for analyzing a real world computer security incident.
I picked a random mail from the work mailbox with an “interesting” attachment. It’s only after running the attachment in a sandbox that I knew it was a version of CryptoLocker.
The message containing the CryptoLocker was received on 4-February 2015. The analysis was done between the 20th and 22nd February 2015.
I first start with analyzing the e-mail. Not everything is relevant for incident response but it does provide the necessary information for setting the scope.
The second part of this analysis will focus on how the CryptoLocker virus behaves and how to extract additional IOCs.
The virus arrives as an attachment to an e-mail
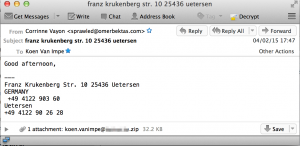
I got a message with subject franz krukenberg str. 10 25436 uetersen coming from “Corrinne Vayon” <sprawled@omerbektas.com>. Below are some of the more interesting e-mail headers. I replaced the e-mail domain with c.d and the receiving host with a.b. The host a.b.c.d is the last receiving e-mail server.
Return-Path: <sprawled@omerbektas.com>
...
Received: from mgtravelpanama.com ([132.248.193.220])
by a.b.c.d. (8.14.4/8.14.4/Debian-4) with SMTP id t14GkkfG007031
for <koen.vanimpe@c.d>; Wed, 4 Feb 2015 17:46:48 +0100
...
Message-ID: <ug1v7h5yt@omerbektas.com>
Date: Wed, 04 Feb 2015 10:47:00 -0600
From: "Corrinne Vayon" <sprawled@omerbektas.com>
X-Mailer: Encumbered v2.94
...
Subject: franz krukenberg str. 10 25436 uetersen
The message pretended to be from someone in Germany and contained one attachment, a zipfile with as name my e-mail address (the koen.vanimpe@c.d.zip)
Content-Type: application/zip; name="koen.vanimpe@c.d.zip" Content-transfer-encoding: base64 Content-Disposition: attachment; filename="koen.vanimpe@c.d.zip"
Mail relay information
If we take a closer look at the e-mail headers we notice that the last mail relay before we (a.b.c.d) receive the mail is mgtravelpanama.com ([132.248.193.220]. The IP address is the only thing that we can fully trust, the domain name is what is set as the HELO of the relaying server. The level of trust you can put in a HELO message depends on the configuration of the receiving mailserver. Some mailservers check if the HELO or EHLO hostname has an A or MX record, other mailservers do not do this check.
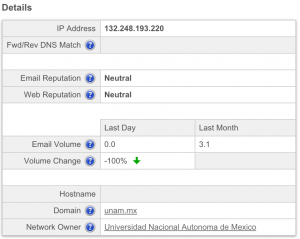
The IP 132.248.193.220 belongs to Universidad Nacional Autonoma de Mexico in Mexico.
inetnum: 132.248/16 ... owner: Universidad Nacional Autonoma de Mexico
According to Cisco SenderBase this IP does not have a bad reputation. It was also not listed in Spamhaus and Spamcop.
The domain used in the HELO of the relay server is mgtravelpanama.com. Although the HELO message should not be fully trusted, it’s still worth having a look at the registration details. This domain is registered in Panama to Sair Sanmartin. It resolves to 199.79.62.54 which is an IP assigned to Confluence Networks Inc in the Texas, US.
Domain Name: MGTRAVELPANAMA.COM ... Registrant Name: Sair Sanmartin Registrant Organization: neutralcargo Registrant Street: rio abajo av la pulida edf rio plaza Registrant Postal Code: 507 Registrant Country: PA ... Net Range 199.79.62.0 - 199.79.63.255 Origin AS AS32787 AS40034 Customer Confluence Networks Inc. (C03095996) Comments Co-located at Data Foundry Austin TX.
The domain was hacked in 2014-05-14 09:12:37 according to Zone-H.
The sender belongs to the domain omerbektas.com. This domain has been registered in Turkey.
Domain Name: OMERBEKTAS.COM Updated Date: 2015-01-05T13:12:49Z Creation Date: 2013-12-08T19:19:03Z Registrant Name: Domain Borsasi Registrant Country: TR
According to the screenshots this domain has undergone a number of changes. The domain was set in 2006 as a placeholder and having a basic site for a fine arts and architecture faculty in 2007. The site seemed to have been renewed in 2009 and was available until 2011. The screenshots show us the domain became available again in 2014. The current registration “Domain Borsasi” means it’s available for purchase (according to Google Translate this is Turkish for ‘Domain Stock Exchange’). One thing to notice is that the last whois update was done early 2015.
The domain now resolves to 78.135.79.27, a Turkish IP assigned to Sadecehosting.
There are a number of references to an Mr. Omer BEKTAS (+ 90 532 4058339) at wakoweb covering something that has to do with kickboxing.
Correspondent information
The From name is Corrinne Vayon. A Google search returns three hits, all in the US with two of them in Florida. There’s nothing useful to learn from this.
- 321-274-8796 – Corrinne Vayon, Ehrler Ln, Winter Park, Florida
- 662-292-1566 – Corrinne Vayon, Brookside Dr, Senatobia, Mississippi
- 352-854-9441 – Corrinne Vayon, NW 40th St, Ocala, Florida
Mail Encumbered
The e-mailer is Encumbered v2.94. I could not find anything worth noting for this mailer.
Message body information
The last thing we can look at it is the content of the mail itself. It pretends to come from Germany, from a town called Uetersen, somewhere in the north of Germany.
The full address is Franz Krukenberg Str. 10 25436 Uetersen. This address belongs to a metal processing company, Metallbau Breutigam GmbH. They have a website that is hosted in Germany at Strato Rechenzentrum, Berlin.
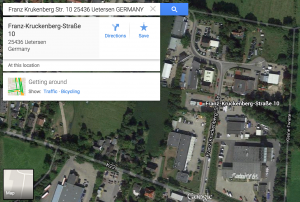
breutigam.de has address 81.169.145.150 ... inetnum: 81.169.144.0 - 81.169.148.255 netname: STRATO-RZG-KA org: ORG-SRA1-RIPE descr: Strato Rechenzentrum, Berlin country: DE
Similar to the From name, this address seems to be randomly chosen and there’s nothing really useful we can learn from this.
Findings
The data in the e-mail header returned some interesting results. There are no country boundries on the Internet. I’m well aware that some of the information has been spoofed but only looking at the e-mail headers shows that Mexico, Panama, United States, Turkey and Germany are involved. It’s not difficult to image that incidents that cover different countries are a nightmare for law enforcement agencies.
| Sender IP address | 132.248.193.220 | Mexico
| Universidad Nacional Autonoma de Mexico |
|
| Sender HELO | mgtravelpanama.com | Panama
| Sair Sanmartin ; neutralcargo |
|
| Sender HELO resolve | 199.79.62.54 | United States
| Confluence Networks Inc |
|
| Sender From | omerbektas.com | Turkey
| Domain Borsasi |
|
| Sender From | Mr. Omer BEKTAS | Turkey | http://www.wakoweb.com/Pdf/10614.pdf |
| Sender From IP | 78.135.79.27 | Turkey
| Sadecehosting |
|
| Postal address sender | Franz Krukenberg Str. 10 25436 Uetersen | Germany
| – |
|
The use of the domain omerbektas.com shows us that attackers reuse abandoned domains, probably hoping that a good (mail-)reputation of these domains allow them easier access to your mailbox.
Peculiar things to notice
The analysis of the e-mail headers learns us that we should block (or at least look closely) at e-mails coming from 132.248.193.220 or having the HELO mgtravelpanama.com or having the FROM set to @omerbektas.com.
| mgtravelpanama.com | Hacked in 2014-05-14 09:12:37 |
| omerbektas.com | No longer used after 2014-02-09 |
| omerbektas.com | Last change at 2015-01-05 |
| attachment | The attachment has a name that corresponds to the receiving e-mail adddress |
Analysis of the attachment
The second part of this post will cover the analysis of the attachment and his behavior.


Hey man, congrats for this great post. The only thing I didn’t understand was how/where you searched for the domain name (mgtravelpanama.com) and got that answer including net ranges.
With my knowledge, I headed to IANA > Domains > .com > Verisign > whois. But I found nothing about IP addressing. Could you tell me how you got that info?
Regards.
The net ranges come from a different query. In the output the first is from whois mgtravelpanama.com, that resolves to 199.79.62.54. Then do http://whois.domaintools.com/199.79.62.54 to get the net ranges.