Magento Vulnerability
Analyzing the Magento Vulnerability
Check Point recently released an analysis of a critical RCE (remote code execution) vulnerability in the Magento web e-commerce platform that can lead to the complete compromise of any Magento-based store, including credit card information as well as other financial and personal data, affecting nearly two hundred thousand online shops.
Magento Patch
Magento already released a patch (SUPEE-5344) on February 9, 2015 (you have to get an account to download the patch, I added it to the security-tools Github repository). On 16th of April, Magento e-mailed their customers urging them to apply the patch immediately.
Magento Shoplift
The bug is dubbed Magento Shoplift by Byte.nl (in Dutch). The Byte Shoplift online check allows you to verify if your website is vulnerable.
A post from Sucuri describes the use of exploit code in the wild.
Inform your constituency?
We had a discussion at work whether or not to inform our constituency. Because we have been running low on available resources and in the past we only sent advisories when it concerns an Heartbleed-ish vulnerable and because the local (.be) impact was fairly low (~500 installations) I considered this as “do not publish”.
Sometimes though it’s good to reconsider so I had a look at how vulnerabilities are measured.
The authoritative source for measuring and scoring vulnerabilities is the Common Vulnerability Scoring System, an open framework for communicating the characteristics and impacts of IT vulnerabilities. The current version is Version 2 but there is a Version 3 in development.
The first place to look for vulnerability information (and the scoring) is the CVE database. Unfortunately the last found entry for Magento is a vulnerability from 2009. This means there’s no ready to use value or metric to evaluate this vulnerability.
Update from @OSVDB and @hanno : there is CVE-2015-1397, CVE-2015-1398 and CVE-2015-1399.
FIRST Common Vulnerability Scoring System Version 3.0 Calculator
FIRST has an online calculator for defining the exact score according to version 3.
I decided to use this calculator together with the document that describes the metrics (December 2014 version).
Base Metrics
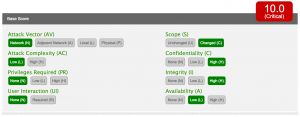
Attack Vector (AV)
This metric reflects the context in which the vulnerability exploitation occurs. For Magento the attack is conducted via the web. This results in a value of Network (N).
Attack Complexity (AC)
This metric describes the conditions beyond the attacker’s control that must occur in order to place the system in a vulnerable state, this also excludes any user interaction requirements. According to Check Point, this attack is not limited to any particular plugin or theme. All the vulnerabilities are present in the Magento core, and affects any default installation of both Community and Enterprise Editions. This results in a value of Low (L).
Privileges Required (PR)
This metric describes the privileges an attacker requires before successfully exploiting the vulnerability, and the potential impact they could inflict on a system after exploiting it. The Magento attack can be done via an unauthenticated attacker. This results in a value of None (N).
User Interaction (UI)
This metric captures the requirement for a user (other than the attacker) to participate in the successful exploit of the target information system. No user interaction is needed for this exploit so this results in a value of None (N).
Scope (S)
This is a conceptual change in the new CVSS. Impact metrics are now scored relative to the impacted authorization scope, or simply Impact Scope. In this vulnerability the attacker can introduce an Administrator account coming from an unauthenticated user. So the resulting metric is Changed (C).
According to @SethHanford a scope “changed” should not be used when privilege escalation occurs, it’s meant to be used when crossing trust boundaries. This would reduce the final score to 9.8.
Confidentiality Impact (C)
This metric measures the impact to confidentiality of a successfully exploited vulnerability. Because the vulnerability can lead to an Administrator account, basically meaning the attacker can do whatever he wants with the Magento setup. This results in a value of High (H).
Integrity Impact (I)
This metric measures the impact to integrity of a successfully exploited vulnerability. Again, because of having an Administrator account, the attacker can change the data at will. This results in a value of High (H).
Availability Impact (A)
This metric measures the impact to the availability of the affected Impact Scope resulting from a successfully exploited vulnerability. Although the attacker can have an Administrator account this does not stop the system from working. In fact, the biggest gain for an attacker from exploiting Magento would be to keep the system running and gathering more valuable user data. I would rate this metric to the value of Low (L).
Temporal Metrics
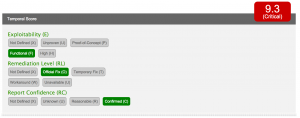
Exploitability (E)
This metric measures the current state of exploit techniques or code availability. Public availability of easy-to-use exploit code increases the number of potential attackers by including those who are unskilled, thereby increasing the severity of the vulnerability. According to byte.nl there is functional exploit code as of 23rd of April. This results in a value of Functional (F).
Remediation Level (RL)
There is a patch available, meaning the metric has a value of Official Fix (O).
Report Confidence (RC)
This metric measures the degree of confidence in the existence of the vulnerability and the credibility of the known technical details. The information from Check Point is reliable and confirmed by the patch of Magenta. This results in a value of Confirmed (C).
Environmental Metrics
Security Requirements (CR, IR, AR)
These metrics enable the analyst to customize the CVSS score depending on the importance of the affected IT asset to a user’s organization, measured in terms of confidentiality, integrity, and availability. This scoring is dependent on the Mangento installation. If the shop is the sole purpose of the site then this would be rated High (H). In other cases, where site-owners sell products but it is not the only main traffic driver for a website then this would result in a value of Medium (M).
Modified Base Metrics
These metrics enable the analyst to adjust the Base metrics according to modifications that exist within the analyst’s environment. These metrics are entirely dependent on the site setup. For example, according to Check Point, their customers are already protected by Check Point IPS. I leave this metric to an undefined value.
Conclusion

Based on the above metrics this vulnerability has a base score of 10.0 – Critical and an environmental score of 9.3 – Critical.
A score this high means Patch! but also issue an advisory!


Thanks for the thorough elaboration! So will you issue an advisory?
See https://www.cert.be/docs/magento-shoplift-vulnerabilty
(contacted sector-organisations asking them to tell their members to go have a look)