Active directory security
Getting Active Directory security right can be a challenging task. Individual groups of computers or user privileges will most likely be properly configured but there are always some trade-offs that have to be made. Attackers will try to find an attack path by abusing the weaknesses that are caused by these trade-offs. Jumping from one host to another, compromising user accounts and abusing active sessions might get them to their final objectives. Whether this is getting a Domain Admin account or gaining access to a system with sensitive data.
Constructing this attack path can be done manually but can also be done via tooling. BloodHound is such a tool.
BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate the same attack paths.
BloodHound uses a number of critical data sets from an AD domain. It uses the Local Administrator groups, the active sessions and the logged on users on domain-joined computers.
Setting up BloodHound
Installing BloodHound is described in detail in the Wiki but some prerequisites are necessary.
PowerShell
Make sure that you run the latest version >=5 of PowerShell. You can easily check this (in PowerShell) with
$PSVersionTable
Upgrading PowerShell requires you to upgrade the .net Framework.
Java
Once that you have PowerShell it’s a matter of installing the latest Java version.
On one of the installs I encountered the error “Could not locate JVM.DLL”
Invoke-Neo4j : Could not locate JVM.DLL at C:\Program Files (x86)\Java\jre1.8.0_181\bin\server\jvm.dll
At line:1 char:299
+ ... t.psd1'; Exit (Invoke-Neo4j install-service)
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
+ FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Invoke-Neo4j
I fixed this by copying the client directory to a server server directory.
neo4j password reset
The installation steps do not mention that you have to reset the password for the neo4j user. You first have to login with user neo4j/neo4j and then change the password. This is described in issue 171.
Running BloodHound
Collecting data via SharpHound
BloodHound first collects the data via an ingestor, writes out the results to CSV files and these CSV files can then be imported in the graphical interface. You can collect the data via a PowerShell script or via an executable (SharpHound). There is also a direct method but building these CSV files can also serve other purposes for post-analysis.
Running SharpHound can take a while, depending on the size of your domain and the requested options.
What is in the CSV files?
A default run of SharpHound creates four CSV files. The filenames pretty much describe their content.
- group_membership.csv
- local_admins.csv
- sessions.csv
- trusts.csv
Import the data
If you’ve previously ran the script in another environment then don’t forget to empty the database! Importing the different CSVs can also take a while.
The BloodHound graph
BloodHound can present the data in two types of graph, hierarchical and directed.
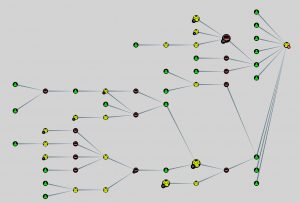
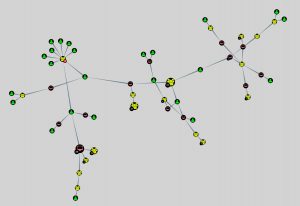
Note that in the screenshots I disabled the option of having the nodes name displayed. In a real-world environment you’ll probably have this option enabled to better understand what nodes (computers or users) you’re looking at.
BloodHound queries
BloodHound (Neo4j) has its own query language: Cypher but also comes with a set of predefined -and very useful- queries.
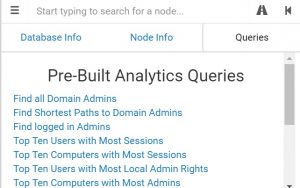
You probably have spotted which query is used most : “Find Shortest Paths to Domain Admins”.
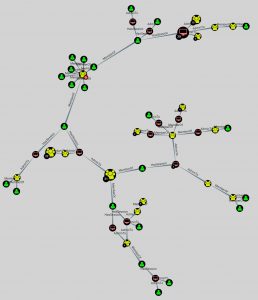
This type of information can show you the most crucial system (or weaknesses) in your environment that would allow intruders to become Domain Admins.
Another interesting query is “Map Domain Trusts”. Abusing the established trusts between domains might allow you to jump from one organization to another.
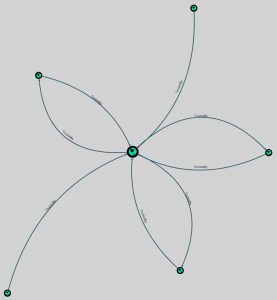
The last query that I wanted to show is “Top 10 Users with Most Local Admin Rights”, showing you which user accounts definitely need account monitoring.
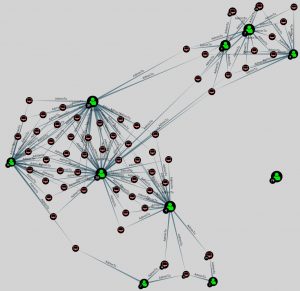
Node information
BloodHound also gives you detailed information for the specific nodes.
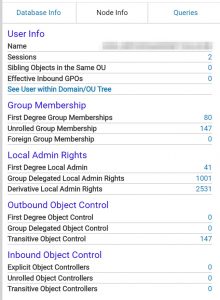
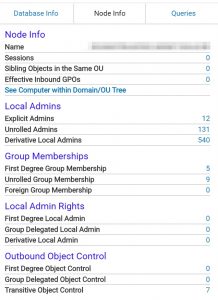
Conclusion
Although BloodHound is primarily seen as a tool for attackers it can also provide great value for defenders and during an incident response process.
- Spot the weaknesses in your AD environment;
- Find user accounts with excessive access to Local Admin;
- Detect system with abnormal high established sessions;
- The CSV files are a great source of information.

