I use a MISP instance to store malware samples that I came across during an investigation or incident. I also worked for example on an integration via a MISP module with the VMRay malware sandbox. The setup with MISP works very well but I needed an easier solution to make these samples available to other users (and tools), without the need of access to this MISP instance.
Enter Malware Repository MWDB, formerly known as Malwarecage. This is a project from CERT.pl that is available as a service (via https://mwdb.cert.pl/login) but you can also host its core component on your own infrastructure. Its features include
- Storage for malware binaries and static/dynamic malware configurations
- Tracking and visualizing relations between objects
- Quick search
- Data sharing and user management mechanism
- Integration capabilities via webhooks and plugin system
My goal with the integration with MWDB was to
- Push samples to MWDB so that I can share/use them more easily during a training;
- Keep the MISP taxonomy (tags) when samples are pushed to MWDB. This allows me to add some contextualisation around the malware samples;
- Use MWDB, or rather its integration with Karton, to have the ability to support different malware analysis backends. Having these multiple backends would greatly reduce the amount of manual work needed. The results of the analysis should still be pushed back to MISP;
- Within MWDB, I wanted a link back to the MISP threat event and in MISP I wanted a link pointing directly to the object in MWDB;
To setup this integration, I wrote a small MISP module for MWDB.
Setting up MWDB
Setting up MWDB is straightforward and described in the MWDB-core documentation. Basically you have to setup a Python virtual environment and then do
pip install mwdb-core mwdb-core configure (create mwdb.ini) mwdb-core run
Apart from the normal configuration of MWDB, the next settings are necessary to have the integration working as expected.
Separate user
Create a separate MWDB user for the integration and create an API key for this user.
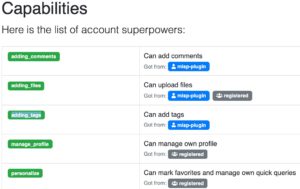
Then assign this user sufficient capabilities. You will need to add adding_comments, adding_files and adding_tags.
MWDB attribute
The link “back” to MISP is achieved with a MWDB object attribute. These attributes (formerly called “metakeys”) are used to store associations with external systems and other extra information about an object.
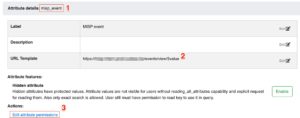
Remember the name (1) of the attribute, you need it later to configure the MISP module. In the URL template (2) add the URL of your MISP instance and add /events/view/$value. The “$value” will be replaced with the MISP event ID. Lastly, do not forget to give your earlier created user the sufficient permissions (3), enable “Read” and “Set”.
MWDB module
Setting up the MISP module
The MWDB module is part of https://github.com/MISP/misp-modules. If you upgraded your MISP modules to the latest version it should be available under Server Settings & Maintenance, Plugin Settings, Enrichment
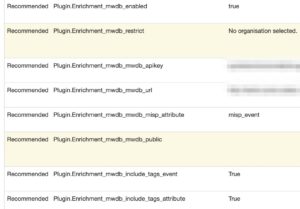
Enable the plugin and add these configuration settings
- mwdb_mwdb_apikey: The API key that you created earlier in MWDB;
- mwdb_mwdb_url: The MWDB URL for API access. This will be along the line of https://yourmwdb:5000/api . It should end in /api. If you access your MWDB instance via “https://my.mwdb.org” this will be “https://my.mwdb.org/api”;
- mwdb_mwdb_misp_attribute: The name of the MWDB object attribute used to link back to the MISP event;
- mwdb_include_tags_event: Set to True if you want to include the tags from the event. Tags with “misp-galaxy” in the name are always excluded;
- mwdb_include_tags_attribute: Set to True if you want to include the tags from the attribute. Tags with “misp-galaxy” in the name are always excluded;
Configuring PyMISP
The module also uses PyMISP to fetch the event information (title) and the tags associated to the event and attachment/malware-sample. To achieve this it makes use of PyMISP. However for PyMISP to function it needs the MISP URL and an API key. The MISP MWDB module expects a keys.py file to be present in /var/www/MISP/PyMISP. You can change this in the code of the module in the variable
pymisp_keys_file = "/var/www/MISP/PyMISP/"
In a next version of the module this should be set as a configuration option from the MISP web interface. The file /var/www/MISP/PyMISP/keys.py needs to contain these variables
misp_url = 'MISP URL' misp_key = 'API KEY' misp_verifycert = True (or False if it should skip the SSL check)
Using the module
The module is an enrichment for two attribute types: attachment and malware-sample. It will return one attribute, a link to the MWDB object.
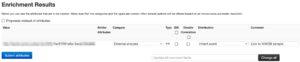
Choose either to (1) propose an enrichment or (2) add an enrichment.
This will then submit the sample to your MWDB instance and add the event and/or tag taxonomy. The result is a proposal for an additional attribute pointing back to the MWDB object.
Output in MWDB
If you then head to MWDB you will see the result of the upload.
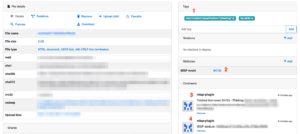
The output contains the (1) tags that were part of the original MISP event/attribute, (2) a link back to the MISP event, (3) the MISP event ID and the title of the event and (4) the MISP attribute UUID.
Remarks
The extraction of malware configuration or the relations features of MWDB are not used. An additional feature of the MISP module could be to include relations between samples if they belong to the same MISP event. Eventually though, these relations and configuration extraction features will be more used by plugging in MWDB into a Karton pipeline.
Instead of MWDB I could also have setup a separate MISP instance that holds only the malware samples. This is not hard to achieve with the proper taxonomy and synchronisation between servers. But because I wanted to have a look at Karton (and integrating it with the CAPE malware sandbox) anyway, MWDB seems as the obvious choice.

