Malware abusing Microsoft Office DDE features
SANS has reported on different malware attacks (Hancitor and Necurs) that abuse the Microsoft Office DDE feature. Similarly, Talos also reported on a malware campaign that used the same technique to get a first foothold in an organisation (DNSMessenger).
DDE is a Microsoft feature now superseded by OLE that allows applications to share data and memory. Usage of the feature does not require a macro and will not show the user a security warning. The only indication for a user is a popup of the Office document requesting to auto update links (if not properly done, the user can also get a warning that an extra application needs to be started). A detailed explanation on how to use DDE (via the DDEAUTO field) is available at https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/.
Note that the attack is not limited to Word or Excel, also Outlook (tasks, calendar invites, RTF e-mails) is vulnerable (and here). In essence the problem is even more serious in Outlook. There is no e-mail attachment to be scanned by the anti-virus. The abuse of the feature can be accomplished by sending a crafted RTF e-mail message.
Prevent and detect DDE abuse
Prevent DDE
You can easily prevent falling victim to malicious documents abusing the DDE feature by disabling it : Disable “update automatic links at open” in Word.
There is also a set of registry keys available, disabling DDE : https://gist.github.com/wdormann/732bb88d9b5dd5a66c9f1e1498f31a1b.
Appearantly the Microsoft Office Attack surface reduction (ASR) doesn’t provide protection (GUIDs BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550, D4F940AB-401B-4EFC-AADC-AD5F3C50688A)
Beware of legacy VBA applications that still rely on the DDE feature.
Prevent against DDE / DDEAUTO attack by micropatching
Update 25-Oct : The people from 0patch created a micropatch for different versions of MS Office (2007, 2010 ,2013, 2016 and 365 (32-bit and 64-bit builds) that protects you against malicious documents abusing this feature. The micropatch simulates a failed CreateProcess, effectively preventing opening a new application (remember, according to the specs “the application name shall be specified in field-argument-1; this application must be running.”).
Detect DDE
Detection of Office documents abusing the DDE feature can be done via a set of YARA rules published by Didier Stevens. Note that there are already reports of documents bypassing the YARA rules via embedding it in different XML tags.
You can also detect the execution of processes from MS Office via Windows event logging. See https://www.securityforrealpeople.com/2017/10/exploiting-office-native-functionality.html
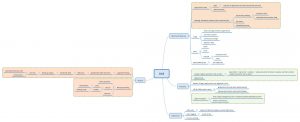
Mindmap on DDE
I created a mindmap summarizing the above information. It is available via Github at https://github.com/cudeso/tools/tree/master/dde-attack.
Updates
- 25-Oct-2017 – 0patching the Office DDE / DDEAUTO Vulnerability… ehm… Feature
- 23-Oct-2017 – Blog showing YARA evasion technique
- 23-Oct-2017 – Added Outlook information
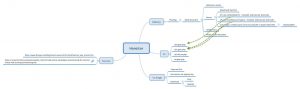
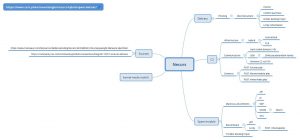
Mindmap on Hancitor and Necurs
For reference, not complete. See https://github.com/cudeso/tools/tree/master/botnets.
Sources
- Macro-less code exec in MS Word
- Talos – DNSMessenger SEC Campaign
- Detecting DDE in MS Office documents
- Exploiting Office native functionality
- MS Office DDE Malware Exploit
- Set of registry keys
- ISC SANS – Necurs
- ISC SANS – Hancitor
- Macroless DOC malware that avoids detection with YARA rules
- Office DDEAUTO attacks
- Using the DDE attack with Powershell Empire


Yes, this is quite a common problem that many people has recently suffered from. Some malware is induced in this Microsoft Office that abuse the features of it and breaks all the security of the users. It is also heard that Microsoft is going to take some actions against it without any delay.