BadRabbit
Another day, another supposedly large scale malware attack. This time it’s called BadRabbit.
Updates
- 2017-10-25 : Detection methods (Windows events)
- 2017-10-25 : YARA rules
- 2017-10-25 : Removed spreading via Eternalblue
- 2017-10-25 : Removed Petya link
Target
Based on the information from ESET the malware targets
- transportation organizations
- governmental organizations
- media outlets
- Russia
- fewer attacks in Ukraine, Turkey and Germany
Delivery (detect and prevent)
The malware is delivered via a fake Adobe Flash update (drive-by attack)
- hxxp://1dnscontrol.com/flash_install.php (block this URL)
- hxxp://1dnscontrol.com/install_flash_player.exe (block this URL)
- afeee8b4acff87bc469a6f0364a81ae5d60a2add
- de5c8d858e6e41da715dca1c019df0bfb92d32c0
According to Kaspersky you should block the execution of the files c:\windows\infpub.dat and c:\Windows\cscc.dat. Disable WMI service (if it’s possible in your environment) to prevent the malware from spreading over your network.
Prevention / vaccination tip : instead of blocking execution you can also preventively create the files (infpub.dat and cscc.dat) and remove all permissions (everyone: deny).
Because the malware will also clear the Windows event log and creates scheduled tasks you should look for the Windows events
- 1106 (clear audit log)
- 106 (new task created), with name drogon, rhaegal
Additional indicators are available via https://otx.alienvault.com/pulse/59ef5e053db003162704fcb2/
There is a set of YARA rules available via https://github.com/Neo23x0/signature-base/blob/master/yara/crime_badrabbit.yar
Exploitation
No exploit takes place, the user has to manually download the file (drive-by attack) and confirm execution.
Installation
The malware requires elevated privileges to run, and uses a Windows UAC prompt to obtain them.
Once installed via the fake Flash update, it will save C:\Windows\infpub.dat and launch it using rundll32. The malware uses Mimikatz to gather system credentials but also contains a set of hardcoded credentials (full list available via https://pastebin.com/01C05L0C). It will then use these credentials to spread further through the network (via WMIC).
infpub.dat encrypts the files (like typical ransomware), installs dispci.exe and launches it via a scheduled task. dispci.exe (DiskCryptor) is a disk encryptor that also modifies the bootloader, preventing a normal boot process after a restart.
According to Costin Raiu it targets similar file extensions but not entirely identical.
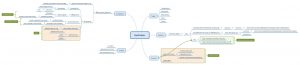
BadRabbit Mindmap
Source : https://github.com/cudeso/tools/tree/master/badrabbit
Sources
- https://www.kaspersky.com/blog/bad-rabbit-ransomware/19887/
- https://www.welivesecurity.com/2017/10/24/kiev-metro-hit-new-variant-infamous-diskcoder-ransomware/
- https://www.csoonline.com/article/3234691/security/badrabbit-ransomware-attacks-multiple-media-outlets.html#tk.rss_all
- https://threatpost.com/badrabbit-ransomware-attacks-hitting-russia-ukraine/128593/
- Vaccination for BadRabbit
- http://blog.talosintelligence.com/2017/10/bad-rabbit.html
- https://www.carbonblack.com/2017/10/24/threat-advisory-analysis-bad-rabbit-ransomware/
- Down the Rabbit Hole: Tracking the BadRabbit Ransomware to a Long Ongoing Campaign of Target Selection
- EternalRomance exploit found in BadRabbit ransomware


There are so many malware, that can be solved if you have a proper solution for that. I really don’t have any idea about badrabbit malware. But I recently face malfunction in my Gmails, and I fix the problem. The thing is after fixing it my Canon printer doesn’t work. It says low ink level. For that issue, I hope you find a suitable solution.