In my previous post I talked about using the nmap NSE scripts or Hydra to search for systems with default passwords. My approach involved two steps: first learn via Burp how the authentication works (getting to know the form elements etc.) and then use this information as input for the brute force scripts.
A colleague pointed out that you can also use Burp suite for this last step.
Attack – Form logins with Burp
Similar as with the previous approach, first configure Burp to act as an interception proxy.
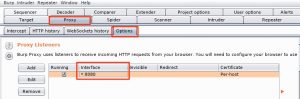
Then use your browser to surf to the web interface that you want to analyze. Once Burp received the form submit request, you can right click the (raw) output window and select Send to Intruder.
Burp Intruder
Burp Intruder is a tool for automating customized attacks against web applications. In this example we can use it to perform a brute force attack with a given list of usernames and passwords.
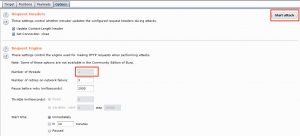
Similar as with the NSE scripts, you have to set the target first. If you used the proxy to intercept the request then this value is pre-filled with the hostname of the request.
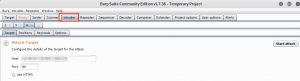
Next you have to tell Burp which elements it has to use during the attack. This step is the same as the manual analysis phase covered in the previous post. Burp will automatically suggest you the form fields that it was able to detect but you can alter these with “add” and “clear”. The fields are separated with a “§” sign.
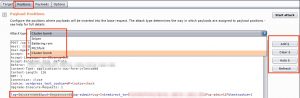
Another important element is the attack type. I require that every username from a list is tested with every possible password (all permutations). This can be done in Burb with the “Cluster Bomb” attack type.
Next we have to set a payload for every detected form field. The payload is the value that will be used by Burp to fill the fields during the attack, in our case the username and password list. You can define a separate payload per element. This means the user list can be attached to the username field and the password list to the password field. First select the element via the Payload set and then give it a list type (Payload Type). Because the purpose is to test for default passwords, including those with a modified case, we can make use of a special list type, the Case modification list.
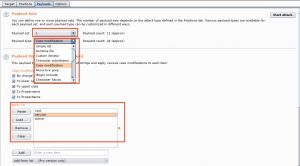
The last step allows you to further tune the attack. As you might have guessed it, Start attack launches the attack.
Attack results
Depending on the size of the list(s) the attack can take a while. When Burp is finished you’ll be able to differentiate the successful and failed attempts by looking at the returned status code and response length. In this case the two requests for admin/admin and root/service returned a different status code (302) and a shorter response length. Most likely these are the successful requests.
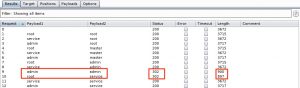
You can also review the details of the requests / responses individually.

Going further
This post only scratches the surface of Burp. Burp also allows you to grep for certain results so you can flag specific result items, making it more easy to spot the successful attempts. You can also configure Burp to follow redirections and process the cookies during redirection.

