MISP and REST API
MISP includes a powerful REST API that allows you to automate the dissemination of threat intelligence and threat data. If you aren’t familiar with the API you can explore its features (and the inline documentation) via Event Actions, REST client.
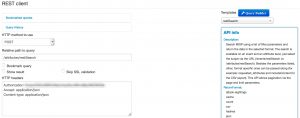
In the latest versions of MISP the REST API client supports autocompletion, which is useful if you want to search for events or attributes with specific tags. And these tags are the vocabularies that we use to classify events and attributes.
Events and attributes
One thing that is sometimes confusing is the difference in results between searching for events and searching for attributes. Hence this small overview.
Searching for events is done via the endpoint events/restSearch. Now if you search for events with tag XYZ then
- If an event is tagged with XYZ, all the attributes of that event are returned;
- If an attribute in an event is tagged with XYZ, then all the attributes of that event are returned. Even if the event itself is not tagged with XYZ.
Searching for attributes is done via the endpoint attributes/restSearch. If you search for attributes with tag XYZ then
- If an attribute is tagged with XYZ, then only that attribute is returned;
- If an event is tagged with XYZ, then all the attributes of that event are returned.

Apart from the tags, there are some other useful selection criteria that you can apply, such as
- type and category: filter on specific MISP types and categories;
- last: return only the results since a given time, for example the last day or week;
- enforceWarninglist: exclude most likely false positives;
- excludeDecayed: exclude the aged out indicators;
- published: only include published data. Note that ‘published’ is only documented for events, but does also work on attributes.
For reference, if you prefer to try out these queries via the command line you can also use this Curl command (which actually queries for the items classified as phishing):
curl -k \
-d '{"returnFormat":"csv","tags":"rsit:fraud=\"phishing\""}' \
-H "Authorization: API-KEY" \
-H "Accept: application/json" \
-H "Content-type: application/json" \
-X POST https://MISP-URL/attributes/restSearch
Additional information is available via the MISP automation documentation.

