PAP and Courses of Action
In a previous article I described how to defend with the courses of action matrix and indicator lifecycle management. The courses of action matrix describes passive and active actions that defenders can take with a varying type of impact on the attacker (or intrusion). The Permissible Actions Protocol or PAP achieves something similar, but with a focus on what defenders are allowed to do.
What is PAP?
PAP is a protocol that describes how much that we accept that an attacker can detect of the current analysis state or defensive actions. It is designed to indicate what the receiver may do with the information and it achieves this by using a colour scheme.
Colour scheme
PAP bears ressemblances with TLP or the Traffic Light Protocol because it makes use of the same colour scheme.
- PAP:RED : Non-detectable actions only. Recipients may not use PAP:RED information on the network. Only passive actions on logs, that are not detectable from the outside.
- PAP:AMBER : Recipients may use PAP:AMBER information for conducting online checks, like using services provided by third parties (e.g. VirusTotal), or set up a monitoring honeypot.
- PAP:GREEN : Active actions. Recipients may use PAP:GREEN information to ping the target, block incoming/outgoing traffic from/to the target or specifically configure honeypots to interact with the target.
- PAP:WHITE : Open, no restrictions
Note that contrary to TLP, where sources can specify additional sharing limits for TLP:AMBER, no such exceptions exist for PAP:AMBER.
For whom?
Foremost, PAP is designed to be used by analysts, operational staff or defenders.
Implementations
PAP is included as a MISP taxonomy and is supported by TheHive.
Practical use
Automation and human consumption
PAP is primarily designed for human consumption. Where the courses of action can be used to automate follow-up actions, for example to automatically create filter deny lists, PAP is rather to be used by humans.
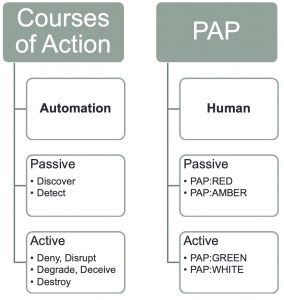
Passive and active
There are overlaps between PAP and the courses of action matrix.
- The distinction between active or passive actions. If you want to prevent that the analysis stage is noticed by the attacker then limit the use of the threat data to passive actions under PAP:AMBER or PAP:RED. Whenever a change (‘active’) is expected, such as filtering traffic (CoA:Deny), use PAP:GREEN or PAP:WHITE.
- Because PAP:WHITE does not add a lot of extra context to threat data it can also be omitted.
- For passive actions. If you’re not allowed to use external systems then use PAP:RED, otherwise PAP:AMBER is fine.
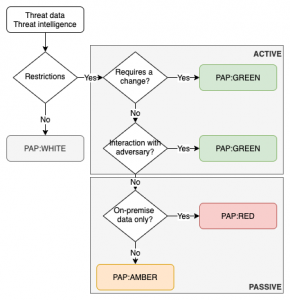
Beware of enrichment
Some automated enrichment process can hinder the proper use of PAP. For example certain SIEMs or anti-virus consoles can do host lookups (DNS) in the background. This almost always involves querying external DNS servers, which can alert adversaries of an ongoing investigation. Note that this is also the case for MISP if you enable the hoover-enrichment plugins.

