Use CryptoLocker to train your incident response team
A couple of weeks back I wrote a post about how to use CryptoLocker to train your incident response team. I waited for another interesting mail and malware sample to arrive to combine the ideas of that post with my post on using different public online malware analyser tools for defining IOCs with online malware analyser tools.
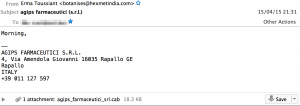
On Wednesday 15-April I received what looked like an interesting mail and attachment to process and analyse.
The idea of this exercise is to quickly extract useful IOCs from malware and the transport media (e-mail) that they use.
E-mail sample
On Wed, 15 Apr 2015 21:31:31 +0200 I received an e-mail pretending to be send by “Erma Toussiant” <botanises@hexmetindia.com> with a subject agips farmaceutici (s.r.l.).
The e-mail was relayed through a Vodafone DSL connection in Italy (188.216.233.135). During the mail delivery the sender announced itself as belonging to geodeticavolpe.com.
Return-Path: <botanises@hexmetindia.com>
...
Received: from geodeticavolpe.com (net-188-216-233-135.cust.vodafonedsl.it [188.216.233.135])
...
Message-ID: <14o0c7kej196u4x@hexmetindia.com>
Date: Wed, 15 Apr 2015 21:31:31 +0200
From: "Erma Toussiant" <botanises@hexmetindia.com>
X-Mailer: Achromatous v2.76
MIME-Version: 1.0
Subject: agips farmaceutici (s.r.l.)
The X-Mailer was set to Achromatous v2.76. This is not a known mailer. According to The Free Dictionary this word means having little or no colour or less than is normal. I assume the mailer name is randomly picked from a dictionary.
The message had one attachment : a CAB file : agips_farmaceutici_srl.cab. The file name of the attachment corresponds with the name of the company displayed in the signature of the e-mail. This is contrary to a previous exercise.
The subject, the attachment file name and the signature displayed in the e-mail reference an Italian company Agips Farmaceutici S.R.L.. As far as I can verify this company is a randomly chosen victim.
According to Cisco SenderBase the IP 188.216.233.135 does not have a bad reputation. It was also not listed in Spamhaus and Spamcop. At first glance, nothing suspicious could be found related to geodeticavolpe.com (the mail HELO domain, registered via a contact in Italy) or hexmetindia.com (the displayed sender domain, registered via a contact in India; one hit was found for hexmetindia.net in an e-mail campaign XLS but that does not seem related).
Analysis of the attachment
The e-mail contained one attachment : agips_farmaceutici_srl.cab.
MD5 = ba914359d9a3f8391fd6165bc6ee41a2 SHA1 = 1d9264321f3f81d0b4d1e814f26904cc2a60a989
A cab file is basically an archive. You can extract these files under Linux with Cabextract. This resulted in one file: agips_farmaceutici_srl.scr.
MD5 = eaff9fe70724e75a78fc7b32553b621c SHA1 = 287aafb8995a28d0873e7659269ef20b7f7ee6a6
The cab file was already analysed by Virustotal. The e-mail with the malware attachment was received on 2015-04-15 21:31:31 GMT+2 and was analysed a couple of hours later at 2015-04-16 05:59:47 UTC by Virustotal. That is a very short delay between arrival of the malware and having it analyzed.
The malware was recognized by 16 out of 56 anti virus products, meaning that there’s a 28% detection rate.
Remarkable, neither Symantec, McAfee or Panda recognized the malware.
With the use of strings I detected that this malware uses these DLL’s
strings agips_farmaceutici_srl.scr |grep dll KERNEL32.dll CRYPT32.dll user32.dll ctl3d32.dll certcli.dll
The CRYPT32.dll is often a sign for some form of ransomware.
Public online malware analyzer tools
Based on the previous information it’s almost certain that this is not targeted malware. I decided to use a number of public online malware analyzer tools to get more information about the behavior of the sample. These tools would help me to get a list of useful threat information and IOCs. I used these online tools to either submit a sample or use the report of a previously submitted sample :
- Virustotal (report only)
- Sophos (report only
- Payload Security (submit)
- Anubis (submit)
- malwr.com (submit)
Both Payload Security and Malwr.com provide screenshots of the malware in action.
These screenshots do not reveal the necessary information that you’re after but it’s always nice to see how malware is “presented” to a victim. These screenshots can also serve in awareness campaigns to warn your constituency.
These samples show that the malware opens Word or Wordpad with a (random?) document.
Virustotal
According to the analysis of Virustotal the malware
- drops or creates a number of files
- C:\DOCUME~1\
~1\LOCALS~1\Temp\hes.cab - ..\a289dd99bd359b89c81f6ea57dae6e77223c1823cfce30fa41da913fc831.rtf
- C:\DOCUME~1\
- Network connection to 191.233.81.105:123
- The file installs an application-defined hook procedure into a hook chain. You would install a hook procedure to monitor the system for certain types of events.
The network connection is a request to a time server located in Brazil, owned by Microsoft Informatica Ltda. There’s nothing suspicious about this request besides getting the “correct” time.
Sophos
According to the analysis of Sophos the malware
- drops or creates a number of files
- c:\Documents and Settings\test user\Local Settings\Temp\kiq.cab
- c:\Documents and Settings\test user\Local Settings\Temp\sample.rtf
- c:\Documents and Settings\test user\Local Settings\Temp\xofam.cab
- c:\Documents and Settings\test user\Local Settings\Temp\hijobo.cab
- uses wordpad.exe
Payload Security
According to the analysis of Payload Security the malware
- has some limited stealthyness and detection for debuggers
- queries the volume information of the harddrives
- drops or creates a number of files
- C:\Users\PSPUBWS\AppData\Local\Temp\qok.cab
- .. a289dd99bd359b89c81f6ea57dae6e77223c1823cfce30fa41da913fc831.rtf
- C:\Users\PSPUBWS\AppData\Roaming\Microsoft\Templates\~$Normal.dotm
- .. ~WRS{26259FF6-15DB-4822-92F5-D00B74F041B5}.tmp
- C:\PROGRA~2\MICROS~1\OFFICE\DATA\opa12.dat
- ..~$89dd99bd359b89c81f6ea57dae6e77223c1823cfce30fa41da913fc831.rtf
- ..~WRS{04A31D66-7DF4-4127-BC95-8E72812F9B4B}.tmp
- queries and modifies registry settings
- does no obvious network connections
- uses winword.exe
Anubis
According to the analysis of Anubis the malware
- converts to agips_farm.exe
- uses wordpad.exe
- modifies registry settings
- drops a number of files
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\agips_farm.rtf
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\mop.cab
Malwr.com
According to the analysis of Malwr.com the malware
- drops a number of files
- ~WRS{65755E2A-A7B7-46E8-A726-0FF2F471B846}.tmp
- ~WRS{CEBD8C18-01E9-42F4-B76B-7F8014D2DE09}.tmp
- ~$Normal.dotm
- agips_farmaceutici_srl.rtf
- rujy.cab
- does no obvious network connections
- queries registry settings
Attachment findings
Dropped files
The attachment drops a couple of tmp, cab and rtf files. The list of dropped files can serve as an IOC to detect local infection
Word or Wordpad
Some of the online malware analysis tools return wordpad.exe and some return word.exe. I assume this is because of the setup of the analysis environments. If Microsoft Office is installed the RTF files are opened with Word, otherwise the system default wordpad is used.
Automatic submission?
The malware sample was analysed by Virustotal in a matter of hours after arrival in the mailbox. Looking at other, similar samples (with minor changes in delivery details) this campaign started around 15-April and was apparently quickly picked up by someone doing the analysis. I do not have information when (or if) the campaign is stopped.
The short timeframe between activation of the campaign an the analysis can indicate some sort of automatic submission.
Interesting to see was that my submission to Malwr.com was the first (no similar submissions based on the hash value could be found).
Network
None of the tools returned network behavior.
Behavior
The DLL used in the malware seem to indicate something similar to a ransomware (CRYPT32.dll) but no network behavior was detected for getting the cryptographic keys.
Most of the detections seem to indicate a flavor of Win32:Kryptik. According to Malwareremovalguides this is a trojan that tries to deploy different other malware.
Based on the analysis of Sophos this is a Trojan.Injector.BID flavor. That is a trojan or backdoor that opens up your computer to other threats.
IOCs and threat information
E-mail findings
The findings below can be used as an IOC but a warning is needed if you use these without context.
The “Sender From IP” belongs to a DSL range in Italy and is probably an infected machine. Instead of blocking individual IPs from a DSL range it is better to rely on some sort of policy block list like the PBL from Spamhaus.
The “Sender From” and “X-Mailer” data are random strings, likely coming from some sort of dictionary, that can easily be changed by the attackers.
Using these as IOCs will block similar e-mail messages. As attackers can easily change the delivery method and e-mail content it’s only only going to provide limited protection. Still, it doesn’t hurt to include them in your detection platform.
| Sender IP address | 188.216.233.135 | Italy | Vodafone Italy |
| Sender HELO | geodeticavolpe.com | Italy | (protected, reseller in Italy) |
| Sender HELO resolve | 62.149.128.x | Italy | Aruba S.p.A. |
| Sender From | botanises@hexmetindia.com | India | Hexagon Metrology India |
| X-Mailer | Achromatous | ||
| E-mail attachment | |||
| Name | agips_farmaceutici_srl.cab | ||
| MD5 | ba914359d9a3f8391fd6165bc6ee41a2 | ||
| SHA1 | 1d9264321f3f81d0b4d1e814f26904cc2a60a989 | ||
Attachment findings
The files created by this malware can be used as an IOC.
| <local user path> | \Temp\hes.cab |
| <local user path> | \Temp\kiq.cab |
| <local user path> | \Temp\xofam.cab |
| <local user path> | \Temp\hijobo.cab |
| <local user path> | \Temp\qok.cab |
| <local user path> | \Temp\mop.cab |
| <local user path> | \Temp\rujy.cab |
Observing the different samples shows that the cab files have more or less random names. A far better IOC would be any new cab file created in the User Temp directory.
Network behavior
No interesting network behavior was observed.
Conclusion
The available online malware analysis tools did not provide conclusive feedback on what this type of malware eventually does to an end-user system. The only way to properly analyze what it does and what impact it has on a system seems to be to run the samples in your own (automated or not) sandbox. More importantly, have a look (and execute) at the dropped files and analyze what they do.
Based on the available reports this attachment drops cab, rtf and tmp files that can download other types of malware to the system. The fact that the original malware already contains the necessary libraries for a ransomware flavor might suggest that the extra downloaded malware is ransomware related. No network behavior was observed in the online reports that suggest downloading of cryptographic keys (typical behavior for ransomware).
Unfortunately, no real conclusive IOCs could be extracted from the online available reports.
Also interesting to see is that neither Symantec, McAfee or Panda recognised the malware.


Have you tried running it for 5-10 minutes with forexample fakenet ?
I reversed some malware VERY similar to this and what it does is sleeps for ~5 minutes and then it starts connecting back to a lot of sites for a extra payload encrypted in a file called “efax.jpg”.
True, for these samples one can let Cuckoo for more than 5 mins to see some more malicious activity.
Wow, that’s what I was seeking for, what a stuff! existing here at this website, thanks admin of this website.
Great post. I’m dealing with a few of these issues as well..