Phishing e-mail
Another day, another phish. This day it concerns a phishing e-mail for a Belgian bank. The phishing e-mail looked like this
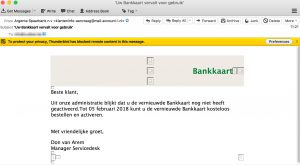
The link is only viewable if you enable HTML content in the e-mail client.
Phishing link
The link points to the URL shortening service Bitly and then follows a couple of redirects (including another URL shortening service).
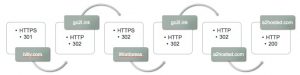
- bitly.com, via HTTPS, received 301 Moved Permanently;
- go2l.ink, via HTTP, received 302 FOUND;
- A PHP page hosted on a WordPress site, via HTTPS, received 302 Moved Temporarily;
- go2l.ink, via HTTP, received 302 Found;
- phishing site, via HTTP, received 301 Moved Permanently (last 302 in graph above should be 301, will update soon);
- phishing site, via HTTP, received 200.
Notice the different redirect codes and the switching between HTTP and HTTPS.
The phishing URL received well above 100 clicks per hour since it was distributed.
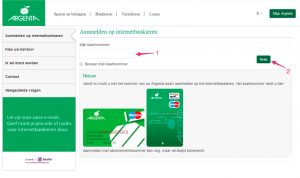
Phishing website
A lot of phishing sites use brand image and CSS files (or direct copies of these files) from the site targeted in the phishing campaign and then combine this with their own HTML. But essentially the phishing site is still basic HTML with some stylesheets and javascript. This method also allows opportunities for defenders to detect these phishing sites (for example direct image requests towards the target or content inspection on unusual web forms on client side).
The phishing website used in this e-mail is a bit different. Not entirely new but because there were quite a few of these messages in my spamtrap I thought it to be useful to have a closer look.
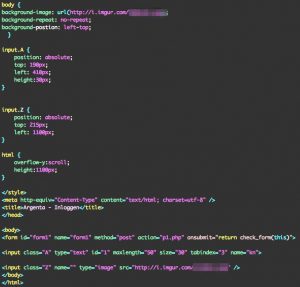
The website is in essence one big image that is set as the background of the web page together with one simple form. The form contains one input field (1) and the submit button is replaced with an image (2). All the form elements have an ‘absolute’ (position: absolute;) position. There’s not a lot of content in the source of the page as a basis for content inspection for phishing.
This is how the HTML looks like, spot the two image references to imgur (background + submit button)
The submit of the form is done via a simple Javascript function.
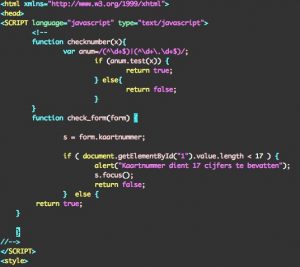
Detection of these type of sites is again a little bit harder.
IOCs
The site has been reported (bank + CSIRT). IOCs are available via Botvrij.eu – Free IOCs via MISP or direct via https://www.botvrij.eu/data/feed-osint/5a722b97-31d8-4e4c-b860-03a7c0a8ab16.json.
Note that Imgur itself is not a malicious website, it’s a photo/imagery website.


I got one for Amazon last year and imgur hosted those yellow “Amazon style buttons”, an Amazon banner with the brand name/logo and even the (German) phishing text was embedded as an image so it passed the spam filter. I wrote to imgur abuse. no reply whatsoever and the images are still available. I would’ve expected them to delete the image with the Amazon logo at least. I didn’t check the source as closely at as you did though. just looked at the raw message source, saw imgur links and opened them. overall it was actually quite well made and I wouldn’t wonder if some people have been phished by that. so I’m really disappointed by imgur. don’t waste your time in trying to contact them