Philips Hue
I recently bought a Philips Hue light system. It allows you to control your lights via a smartphone app and set the right colour mood. Setup is easy, you connect a light bridge to your home router, connect with the app and then setup the lights. The system also includes an API to build your own apps.
Use Snort to detect malicious code
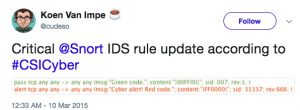
In 2015 I tweeted on an episode of CSI Cyber where “good” code automagically turned green whereas “bad” code turned up red : Critical @Snort IDS rule update according to #CSICyber.
So why not use the Philips Hue system to mimic this environment?
Workflow
The workflow I came up with is Snort > Syslog > External app > Philips Hue
Custom ruleset for Snort
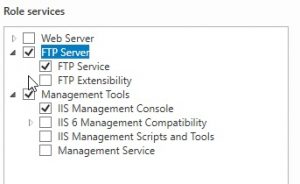
The first part to configure is setting up Snort. This is easy with Ubuntu
apt-get install snort
For my experiment I only needed two rules. I disabled all other IDS rules in the snort config file (/etc/snort/snort.conf) and included my own ruleset. In snort.conf :
include $RULE_PATH/cudeso.rules
And then the actual rules :
alert tcp any any -> any any (msg:"CustomDLP : Access to mysecretfile"; content:"mysecretfile"; sid:990001; rev:6;) alert tcp any any -> any any (msg:"CustomSafeDLP : Access to safefile"; content:"safefile"; sid:990002; rev:1;)
Basically what these rules do is alert on every connection to either “mysecretfile” or “safefile”.
Syslog logging for Snort
Snort needs to be configured to log to syslog. Do this in the config file with
output alert_syslog: LOG_AUTH LOG_ALERT
Note that snort logging to syslog on Ubuntu systems is in the file /var/log/auth.log.
Rsyslog
How do I get from Snort alerting to switching on the light bulb? Snort is able to log to syslog. In my case I use rsyslog. Rsyslog is able to execute custom applications based on certain log events.
In /etc/rsyslog.conf add these lines
module(load="omprog")
if $rawmsg contains "snort" then
action(type="omprog"
binary="/home/koenv/philips.py"
template="RSYSLOG_TraditionalFileFormat")
This configuration setting will launch the script “philips.py” (in my home directory) whenever an event is found that has the string “snort”.
Configure your light bridge
The Philips site has a detailed explanation on how to get API access to your light system : Getting started with Philips Hue. You need to get your user ID (the authentication string, notice that this is all in HTTP) and the ID of your light bulb.
The Philips Hue script
So far we have Snort alerting on our custom rules, generating an alert in syslog and then rsyslog executing an external application.
Rsyslog has a good skeleton that describes how you should build your external custom alerting application : https://github.com/rsyslog/rsyslog/blob/master/plugins/external/skeletons/python/plugin.py.
Because this is a proof of concept I didn’t really needed the throttling in processing the messages. I used my script below
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import sys
import requests
import json
import time
SYSLOG_ALERT="CustomDLP"
SYSLOG_PASS="CustomSafeDLP"
LIGHT_BRIDGE = "192.168.x.x"
LIGHT_ID=5
LIGHT_USER_ID="your-philips-hue-id"
LAMP_RED={"on": True, "xy":[0.65,0.25]}
LAMP_GREEN={"on": True, "xy":[0.1,0.8]}
def lamp_on(lampid, payload):
url = "http://%s/api/%s/lights/%s/state" % (LIGHT_BRIDGE, LIGHT_USER_ID, lampid)
r = requests.put(url, data=json.dumps(payload))
def lamp_off(lampid):
url = "http://%s/api/%s/lights/%s/state" % (LIGHT_BRIDGE, LIGHT_USER_ID, lampid)
payload = {"on":False}
r = requests.put(url, data=json.dumps(payload))
syslogline = sys.stdin.readline()
if syslogline.count(SYSLOG_ALERT) > 0:
lamp_on(LIGHT_ID,LAMP_RED)
time.sleep(2)
lamp_off(LIGHT_ID)
elif syslogline.count(SYSLOG_PASS) > 0:
lamp_on(LIGHT_ID,LAMP_GREEN)
time.sleep(2)
lamp_off(LIGHT_ID)
The script does two things depending on the Snort alert :
- If it contains the string “CustomDLP” (defined in SYSLOG_ALERT) it will set the light to red;
- If it contains the string “CustomSafeDLP” (defined in SYSLOG_PASS) it will set the light to green;
Finishing the setup
Restart rsyslog and launch Snort, either via your normal startup scripts or via the command below. The -i indicates the interface Snort has to monitor.
/usr/sbin/snort -m 027 -u snort -g snort -i ens33 -c "/etc/snort/snort.conf"
Philips Hue as an IDS
The previous commands started Snort, had it log to syslog and then have rsyslog execute an external command. Now it’s about time to test this setup. In another console try
wget www.google.com/mysecretfile
or try
wget www.google.com/safefile
Philips Hue as IDS from Koen on Vimeo.
Where to go from here?
I strongly recommend you not to switch on your light bulbs for every single IDS alert. However setting up the IDS rules for triggering on access on very specific files or requests can be useful. And even if it’s not that useful, it makes great pictures for a war-room!